


In our modern threat landscape, it is common for threat actors to design malware from scratch to evade standard security tools. Default rulesets like those provided in Datadog's Workload Protection are no exception.
Modern endpoint protection products and standard SIEM defaults typically only detect known threats, or maybe you’ve identified visibility gaps in your security posture. Truly bespoke threats often bypass out-of-the-box rule sets. To close this gap, security teams follow a recurring lifecycle:
In the following sections, we’ll walk through a simplified variant of this process, enabling even less-experienced engineers to use a malware sample to create targeted Datadog rules for hardening your environment.
We will examine an active malware named "Myth Stealer," an info-stealer designed to covertly gather information and exfiltrate it to a command-and-control (C2) server. Typically delivered through social engineering, info-stealers are straightforward to detect due to their predictable data-exfiltration methods.
For this article, assume this malware was identified during incident response for unauthorized access using stolen browser credentials. The sample was retrieved from the user's Downloads folder and secured for analysis.
The simplest approach to reverse engineering malware is to observe its behavior. A secure, isolated environment is essential for this step. A recommended tool for basic malware analysis is Triage, a free service that allows secure uploading, execution, and analysis of malware samples.
This tool sufficiently automates dynamic analysis for you, useful for the purpose of identifying Indicators of Compromise (IoCs) and creating relevant detection rules.
After analysis, Triage will include a breakdown of significant indicators, such as file modifications, network connections, etc, enabling you to clearly understand and address the threat.
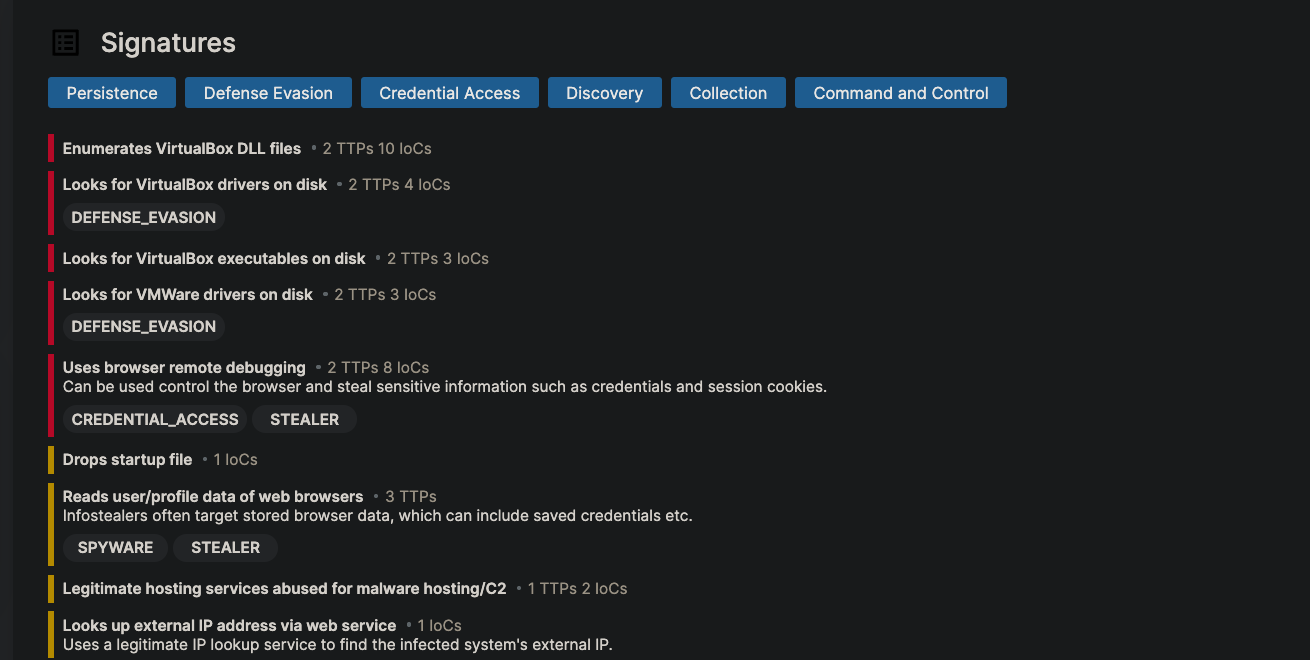
Identifying IoCs requires analytical consideration. Key actions performed by this specific sample include:
A low-hanging fruit approach to creating effective detection rules is focusing initially on the data-exfiltration process itself, which tends to follow predictable patterns across various malware families. Since these exfiltration methods are common and consistently applied, detection rules developed around these techniques likely provide broad protection against similar threats as well.
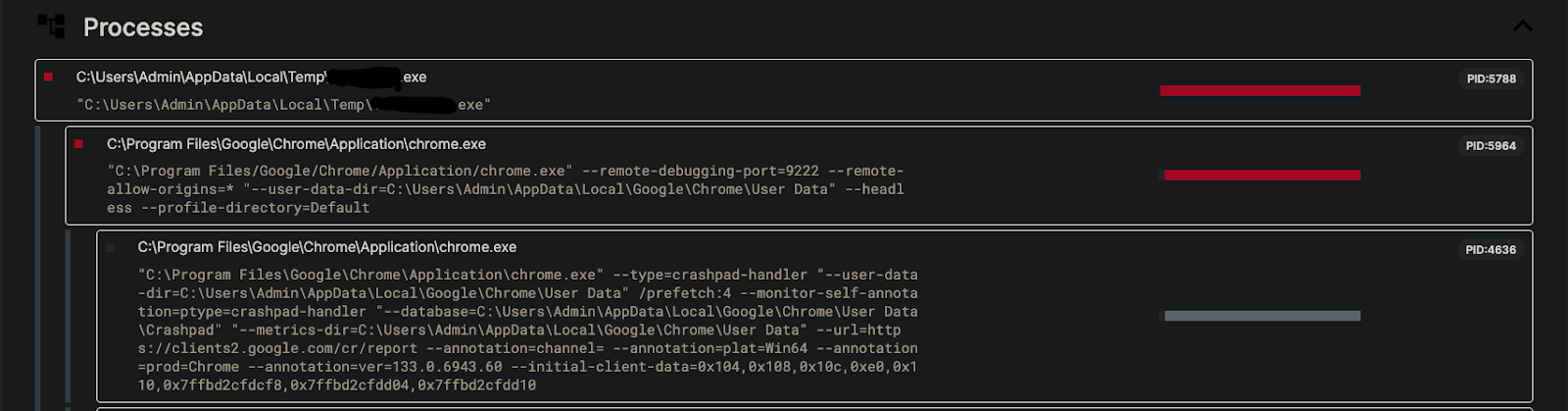
Observing the malware’s process tree reveals it spawning a subprocess of Chrome immediately after execution. We will craft a detection rule targeting processes run from specific directories that initiate Chrome with remote debugging flags.
Following Datadog's guidelines for Creating Agent Rule Expressions, we create the following rule to capture the described behavior:
This rule detects any process (Chrome, Edge, Brave, etc.) started with the "remote-debugging-port" flag from directories commonly used by the malware family, indicating potential user-initiated malware.
To deploy this rule:
Triggered events will appear in the Agent Events Explorer.

Ideally, testing should involve deploying the Datadog agent within a secure sandbox environment where the detection rules are already configured. In this environment, safely detonate the malware sample and verify that Workload Protection correctly identifies and logs its behaviors. However, to minimize risk in this demonstration, we'll instead use a simplified Go-based simulation that replicates the behavior of launching Chrome with the debugging flag, avoiding the need to execute actual malware samples directly.
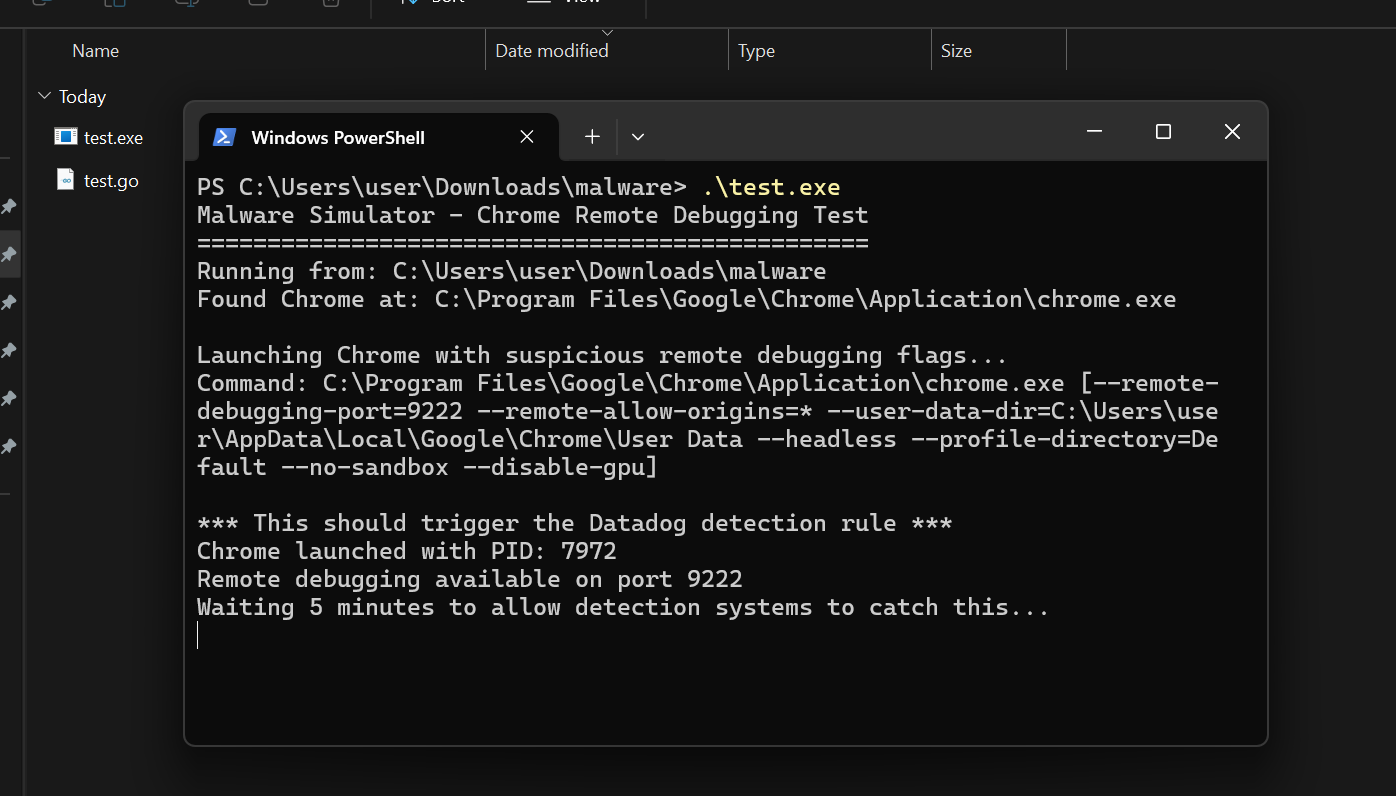
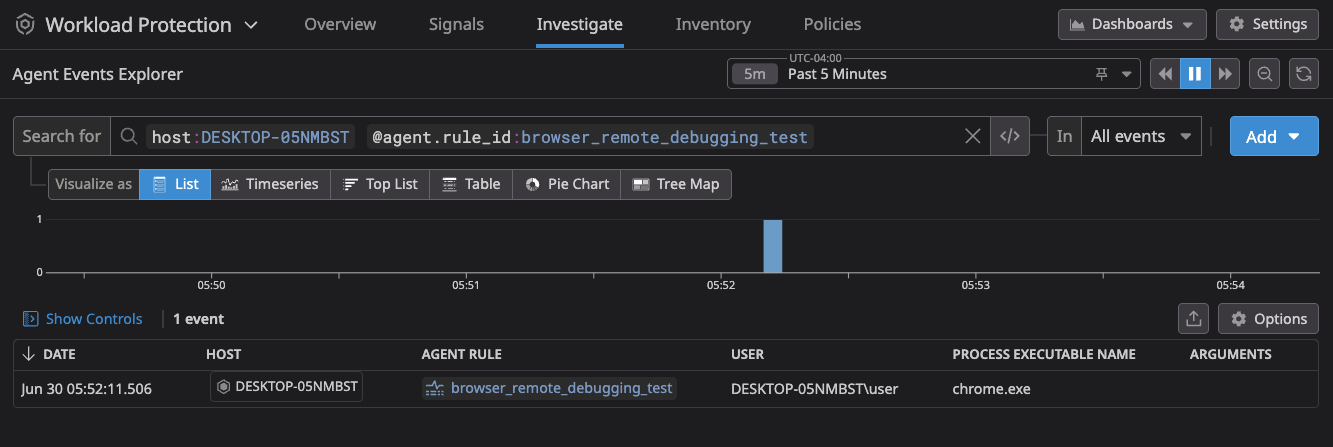
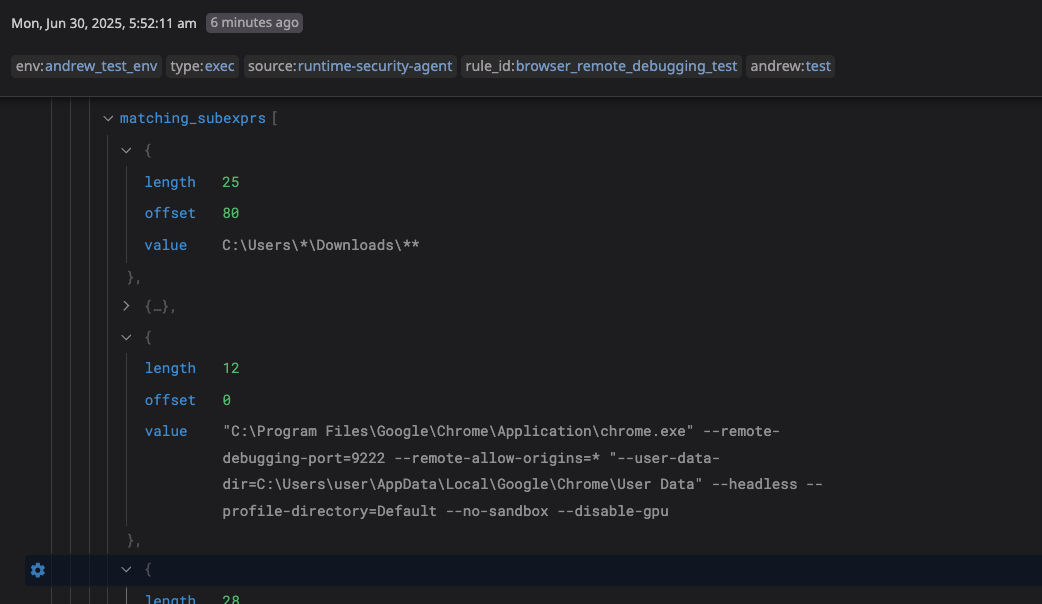
Upon running this test, the Workload Protection "Agent Events Explorer" immediately detects the event. Details confirm detection from the downloads folder and the debugging flag.
Implementing a detection rule is just the start—it's crucial to continuously monitor your environment and iteratively improve your security measures. Organizations embracing continuous monitoring drastically reduce detection and response times, making it harder for attackers to establish a foothold.
To maximize the value of your Datadog Workload Security policies, leverage Datadog’s built-in threat intelligence to keep up with the latest intel:
By following these proactive steps, your organization shifts from reactive security measures to a robust, proactive stance, significantly enhancing your overall security posture.
Managing and continuously refining detection capabilities requires resources and expertise—that’s where RapDev can help. Our team provides specialized support for all Datadog security modules, assisting organizations through every stage of the detection lifecycle. RapDev focuses on collaboration to streamline your processes and optimize your effectiveness. Ready to strengthen your security posture? Contact us today and unlock the true potential of your security teams.
We go further and faster when we collaborate. Geek out with our team of engineers on our learnings, insights, and best practices to unlock maximum value and begin your business transformation today.
End-to-end visibility, resilience, and cost-efficient observability for always-on financial platforms

Building the observability foundation required for AI to reason across your stack
