


Effective threat hunting is about clarity — not guesswork. When authentication data is messy or incomplete, identifying real threats becomes slow and unreliable. With Datadog’s advanced log management and Cloud SIEM capabilities, teams can turn raw authentication logs into high-confidence security signals that actually drive action. Before diving into detection, it's essential to outline the best practices for generating authentication logs.
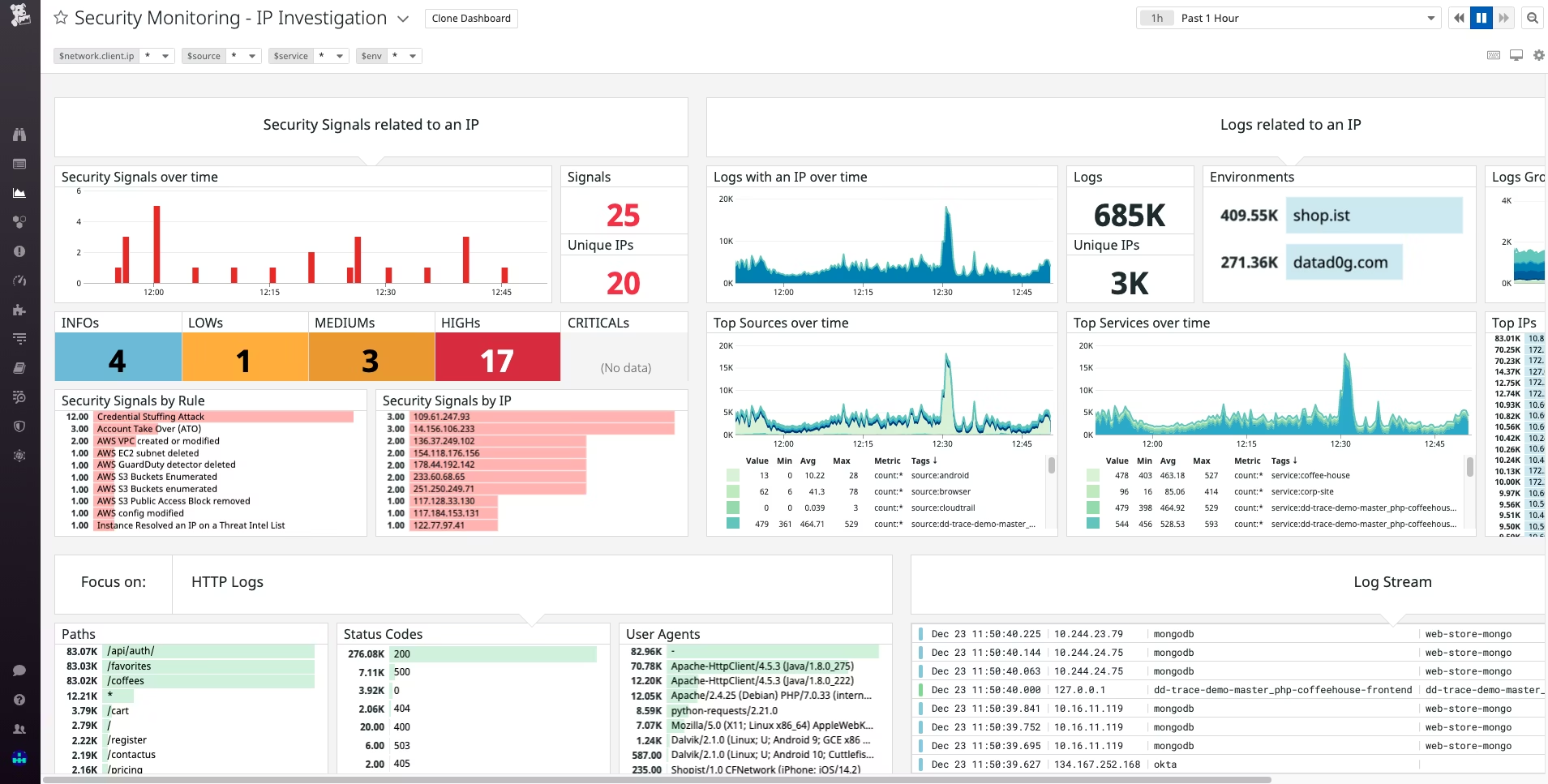
Datadog Cloud SIEM continuously scans 100% of ingested logs using built-in detection rules aligned to common attacker techniques. When suspicious activity is detected, Datadog generates a Security Signal with contextual details, severity, and response guidance. Pre-built dashboards—like the IP investigation dashboard and User investigation dashboard - simplify identifying trends. These trends include things such as spikes in failed login attempts or unusual access patterns, which are shown in the screenshot below.
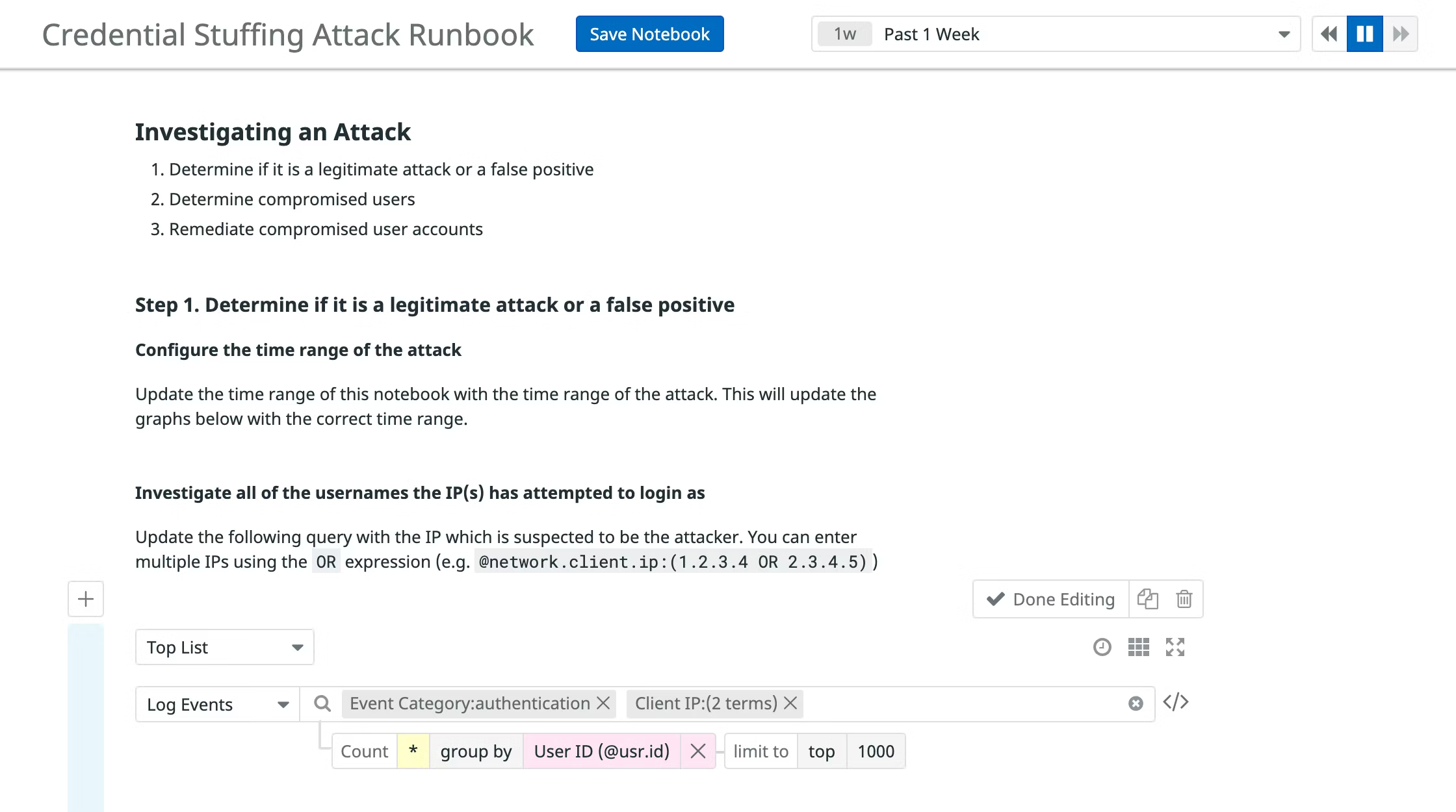
Datadog offers out-of-the-box runbooks, such as the one for credential-stuffing investigations, as illustrated in the screen shot below.
Datadog’s log processing pipelines enrich authentication data in real time. For example, the GeoIP parser extracts geographic details from IP addresses, enabling detections like unexpected login locations or impossible travel detections rules. This feature is shown in the screenshot below.
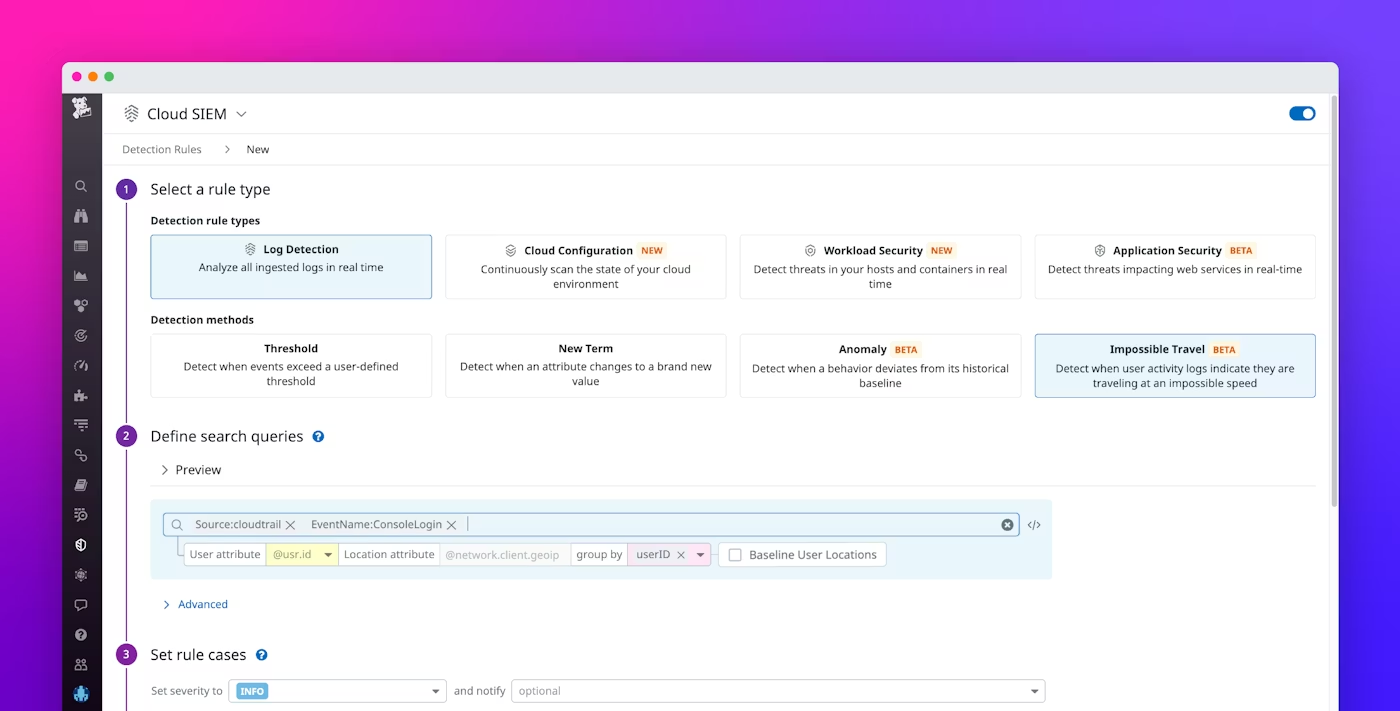
Similar to Datadog's standard threat detection rules, the impossible travel detection rules leverage Datadog's log search syntax. This allows you to specify the logs you wish to monitor easily. This added context (user, IP, country, city) significantly improves detection accuracy and reduces false positives, helping security teams focus on real threats faster. The results are presented as a Security Signal, enabling teams to rapidly identify and investigate potential authentication attacks, as illustrated in the screenshot below.
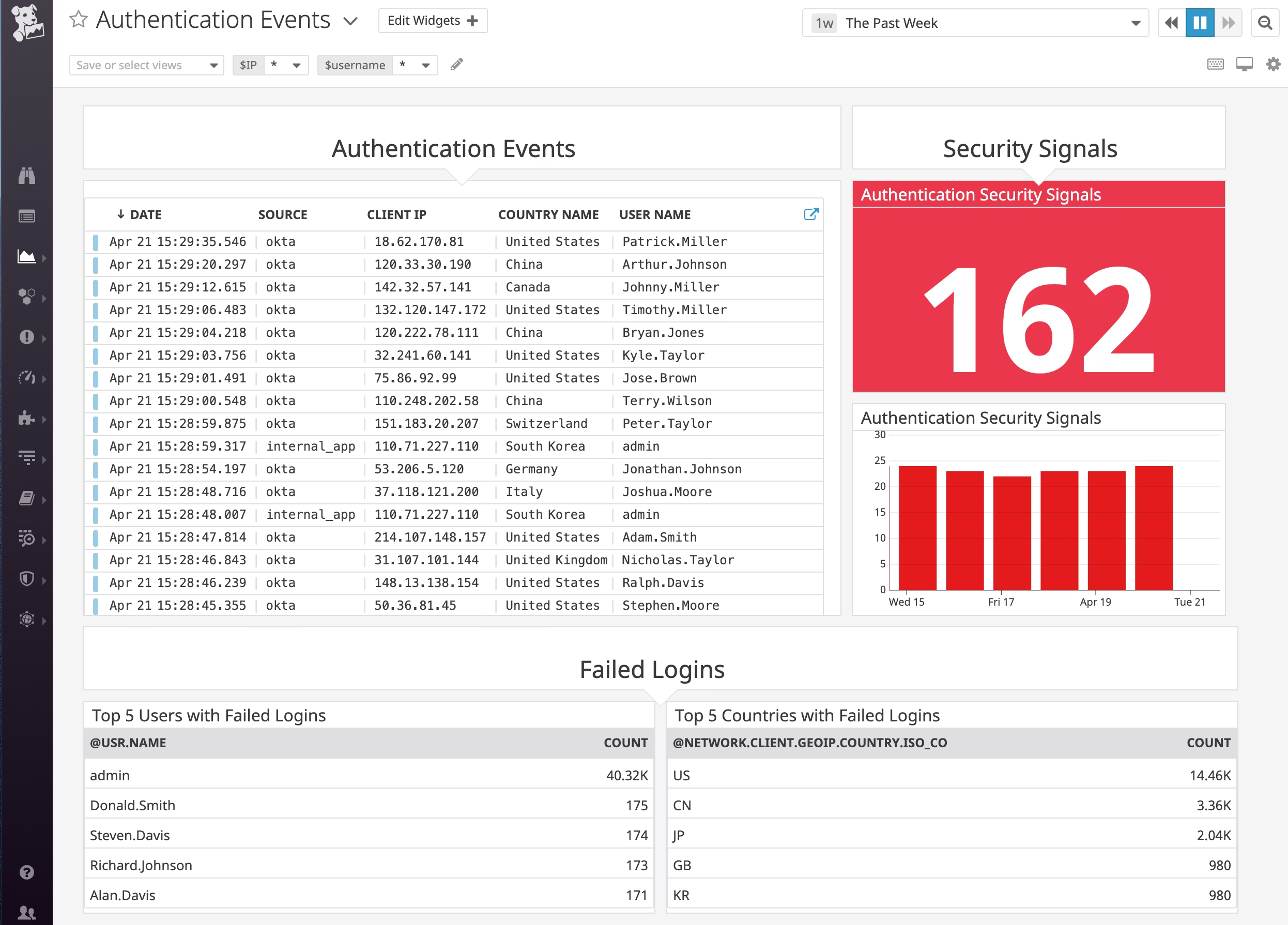
A security signal includes crucial event data, such as the type of attack detected and suggested response strategies. You can effectively triage and prioritize your focus by easily viewing, filtering, and sorting all Security Signals within the explorer.

Unstructured string logs slow down investigations. By logging authentication events in key-value format and using Datadog’s Grok Parser, teams can extract consistent fields such as user IDs, outcomes, and IP addresses.
Essential Authentication Attributes
usr.id – Unique username or emailevt.category – Set to authenticationevt.name – Login method (SAML, OAuth, etc.)evt.outcome – success or failurenetwork.client.ip – Source IP addressWith these fields in place, detecting common authentication attacks like brute force attempts or credential stuffing becomes straightforward and reliable. The image below displays a defined search query. This query is designed to correlate failed and successful login events, allowing for the detection of credential stuffing and the prioritization of authentication threats with a high degree of confidence.
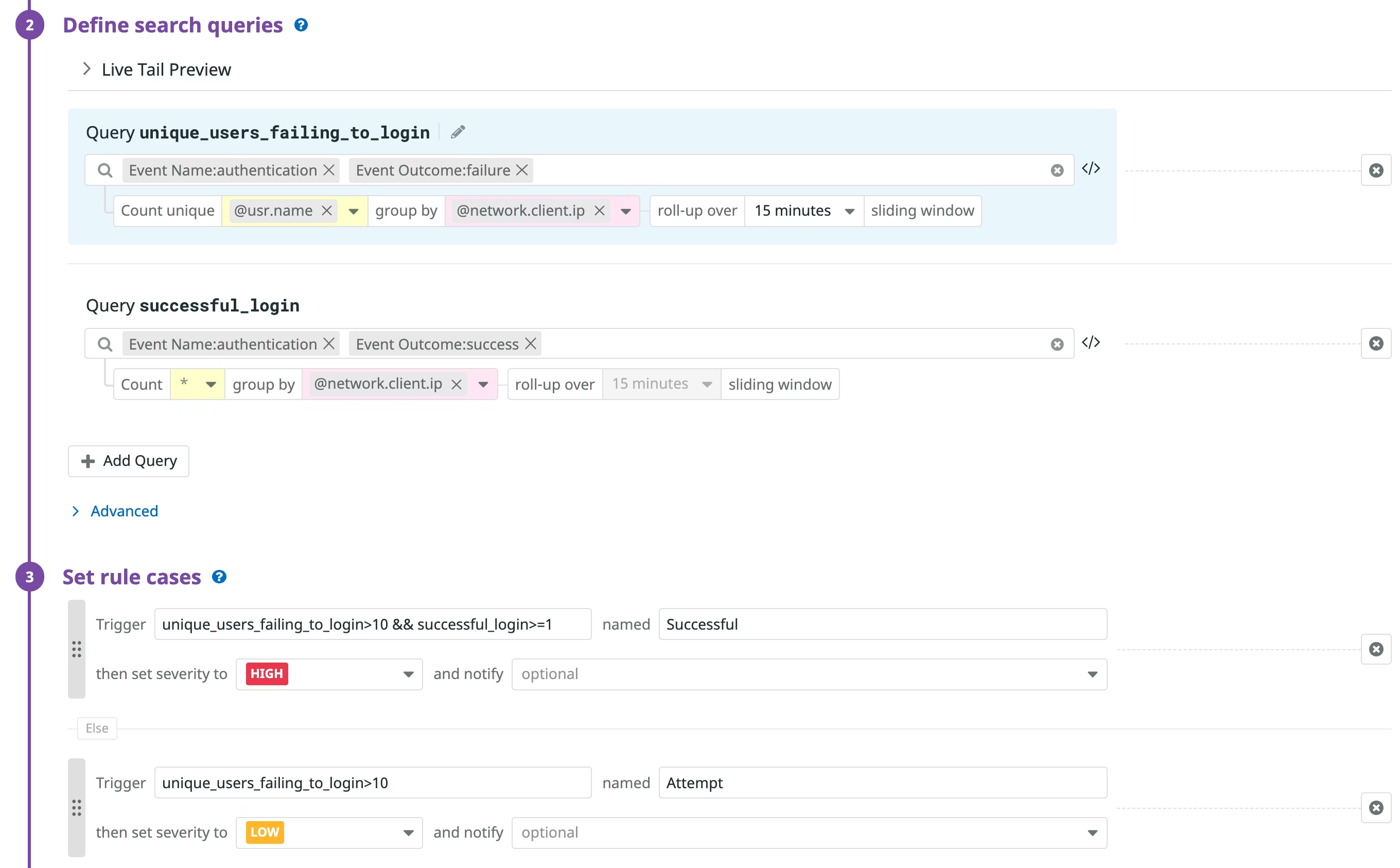
Effective threat hunting relies on clean authentication logs, enriched context, and detections you can trust. By using Datadog Cloud SIEM, log pipelines, and structured fields, teams can quickly identify suspicious login activity and focus on real risk. If authentication threat hunting is still noisy or unreliable in your Datadog environment, contact RapDev.
We go further and faster when we collaborate. Geek out with our team of engineers on our learnings, insights, and best practices to unlock maximum value and begin your business transformation today.
Scaling detection engineering in Datadog with detection as code, git workflows, and operational guardrails

How Datadog Cloudcraft visualizes cloud infrastructure for security, cost optimization, and governance
