

Cloud security monitoring usually starts with identity, network, and workload telemetry: who logged in, what changed, and where data moved. But there’s another enterprise signal that often sits in a different org and arrives “after the fact”: cloud spend. This post explores a simple idea: Does cost tracking help highlight certain cases of abuse? Not as proof of compromise, but as an additional lens that can help monitoring…or maybe even close a gap? I’ll go as far as to say cost tracking may even have a spot in the defense-in-depth approach.
A lot of financially motivated cloud attacks are literally designed to consume resources. Cryptojacking is the obvious example: attackers abuse your computer to mine cryptocurrency. That means the victims are fronting the costs. Most researchers and cloud security vendors have written about this. It’s essentially “compute resource abuse,” and the victims can incur substantial fees from compromised tenants. Sysdig’s threat research puts a sharper point on the economics, estimating that attackers can cost companies hundreds of thousands of dollars in cloud bills to generate a pretty small crypto revenue. As attackers get better at evading rule-based detections, machine learning threat identification techniques, and AI-supported security operations, cost will forever be something they cannot hide. Someone has to pay (money, that is).
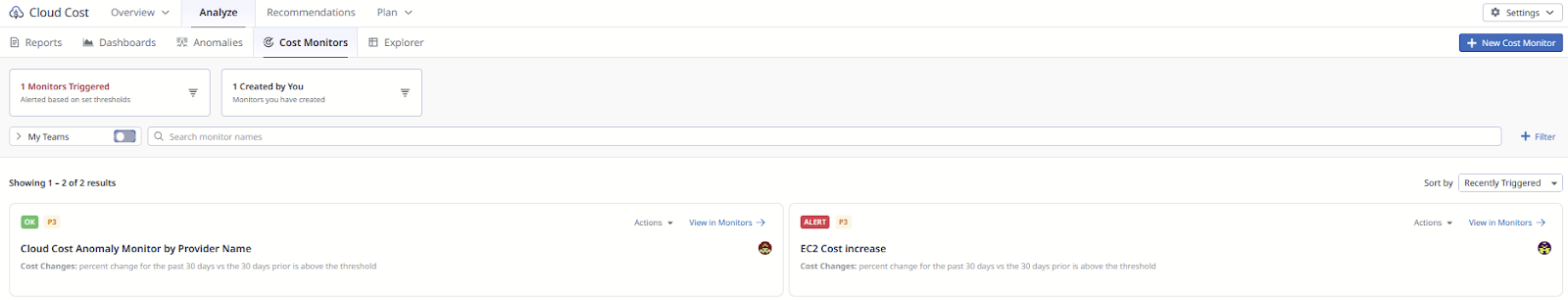
Cost isn’t a perfect security indicator, though. Launching new nodes for a product deployment can look the same as launching them for cryptomining—until you correlate. That’s where Datadog’s Cloud Cost Management (CCM) becomes interesting: Datadog ingests cloud cost data and transforms it into metrics you can query, explicitly encouraging correlation between cost increases and usage metrics to find the root cause. The Cloud Cost Explorer is built for ad-hoc investigation of trends and anomalies across providers. When you want repeatable detection, Cloud Cost Monitors let you alert on cost changes and threshold breaches. You can also set budgets at a monthly level by cloud provider or leverage the myriad of other tags and attributes available. The idea here is to lean into cost monitoring as an early warning boundary when routed to the right responders. If you take that analysis another step deeper, you could even find that “why does this even exist?” infrastructure.
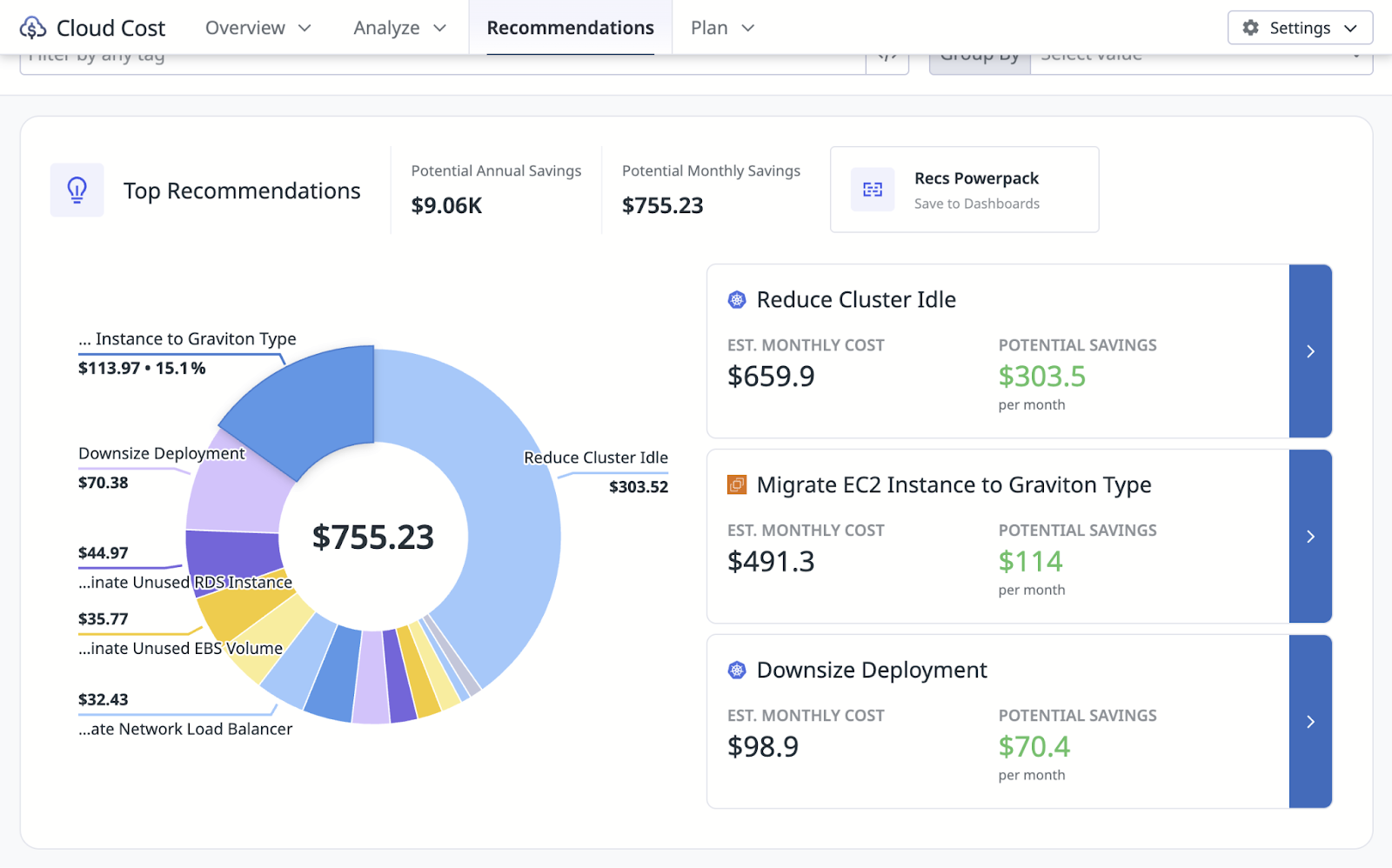
The idea here is not to claim that cost monitoring is a mandatory piece of your defense-in-depth strategy. The takeaway is really to reframe something you are already conscious about, money, and leverage it as a supporting signal. Think about piping cost anomalies into the same SOC workflows as identity and infra alerts. Push to require ownership tags so “unknown spend” is actionable. Maybe build a playbook to ease correlation, like cost spike → investigate for new resource deployments → identify events → correlate to the owning team. You may not catch every attack with cost; in fact, you likely won’t catch every attack because of cost monitoring. But that is not the point. The point is, maybe tracking spending can help fill a monitoring gap or be a data point available for better correlation. Try it out and see how it works for your organization!
RapDev lives and breathes Datadog engineering. And we don’t just claim that – we have years of experience working with organizations around the world, big and little, new to Datadog and not. RapDev has an answer to any problem you have, so let’s build something better together! If you need Datadog implementation assistance, need to optimize your spend, or need a trusted security partner, contact us today.
We go further and faster when we collaborate. Geek out with our team of engineers on our learnings, insights, and best practices to unlock maximum value and begin your business transformation today.
Scaling detection engineering in Datadog with detection as code, git workflows, and operational guardrails

How Datadog Cloudcraft visualizes cloud infrastructure for security, cost optimization, and governance


